-
PDF
- Split View
-
Views
-
Cite
Cite
Eric Hines, Shivang Trivedi, Cindy Hoang-Tran, Joseph Mocharnuk, Miles J Pfaff, Perspectives on Cybersecurity and Plastic Surgery: A Survey of Plastic Surgeons and Scoping Review of the Literature, Aesthetic Surgery Journal, Volume 43, Issue 11, November 2023, Pages 1376–1383, https://doi.org/10.1093/asj/sjad122
Close - Share Icon Share
Abstract
Data breach costs in the United States are among the highest in the world, making robust cybersecurity an important bulwark of national defense. Healthcare is a popular target for cyber threats, and there is increasing emphasis on cybersecurity safeguards to protect sensitive patient data.
The objective of this national survey and scoping review is to (1) identify cybersecurity awareness, preparedness, and practices among plastic surgeons, and (2) to provide guidelines to mitigate the threat of cyberattacks.
A 16-question, anonymous online survey was developed and distributed to The Aesthetic Society registrants to ascertain plastic surgeons’ cybersecurity practices. Utilizing PubMed, CINAHL, and Embase databases, eligible articles were identified as part of this scoping review.
Of 89 individuals who began the survey, 69 completed it (77.5%). Sixty respondents agreed or strongly agreed that cybersecurity is an important issue in plastic surgery. The greatest perceived limitations for protection against cyberattacks were insufficient expertise (41.7%), followed by lack of funding and insufficient time to dedicate to this goal. Most respondents (78.7%) had cybersecurity policies incorporated into their practice. Those who agreed or strongly agreed they had technology to prevent data theft/breach were significantly more likely to be older than 54 years of age (P < .001). No articles identified in the literature specifically addressed cybersecurity in plastic surgery; however, 12 articles detailing cybersecurity in healthcare were identified and included.
Despite possessing adequate technology and procedures in place to prevent cyberattacks, plastic surgeons perceive significant barriers to cybersecurity protection, including insufficient expertise and lack of dedicated funding. It is imperative that our field establishes standards and protocols to protect our patients.
Healthcare represents a critical pillar of US industry and infrastructure. Over the past few decades, the US healthcare system's increasing reliance on information technology, especially in the form of electronic health records (EHRs), has necessitated strict federal regulations concerning the safeguarding of patients’ protected health information (PHI). Of the many kinds of data breaches, PHI breaches constitute the most expensive category in the United States for the past 12 years running, costing an estimated 10 million dollars per breach in 2021.1 The complexity of our healthcare system and its variegated technology, including cutting-edge software and aging record and storage systems, make it a particularly vulnerable target. In 2020, the University Hospital of New Jersey paid a $670,000 ransom to prevent the leak of stolen PHI.2 Although common sense dictates that large institutions are capable of larger payouts, smaller practices can also be lucrative targets for cybercriminals.
Among medical and surgical specialties, plastic surgery practices are arguably unique, as they serve a broad patient population with, often times, highly sensitive information and photographs. Thus, plastic surgery practices’ possession of detailed documentation, including before and after photographs of patients, can make them an attractive target to those intent on exploiting PHI for profit.3
Despite an increase in cyberattacks targeting healthcare organizations and practices over the past decade,4 there are no standardized cybersecurity policies and procedures in place for plastic surgery practices to follow. To assess plastic surgeons’ understanding and implementation of preventative cybersecurity practices in the United States, a survey was deployed utilizing The Aesthetic Society's national registry. A scoping review was also performed, with the objective of identifying evidence detailing cybersecurity within plastic surgery and healthcare that could be utilized to inform best practices within the plastic surgery community.
METHODS
Survey
A 16-question, anonymous online survey was developed and deployed to The Aesthetic Society online registrants to ascertain various aspects of cybersecurity practices among plastic surgeons. The survey was composed of 5 general areas: (1) having established cybersecurity policies; (2) dedicated technology and personnel to prevent an attack; (3) prior security breaches or attacks; (4) limitations to preventing a cyberattack; (5) if cybersecurity is an important issue in plastic surgery (see Appendix, available online at www.aestheticsurgeryjournal.com). The survey was placed online using software from Qualtrics (Provo, UT). An email with a cover letter was generated and sent to all 1645 members on September 22 and November 2, 2022. Responses from the survey questions were recorded and tabulated using Microsoft Excel (Microsoft, Inc., Redmond, WA). For outcomes analysis, the total responses for each question were totaled. For investigation of statistically significant associations between variables, multiple ordinal logistic regression was utilized using RStudio (Postit Software, Boston, MA) (Version 2022.07.1+554 “Spotted Wakerobin”).
Scoping Review
A scoping review of cybersecurity in plastic surgery and healthcare was conducted using PubMed, Cumulative Index Nursing and Allied Health Literature (CINAHL), and Embase (Elsevier) databases adhering to Preferred Reporting Items for Systematic Reviews and Meta-Analyses (PRISMA) guidelines (Figure 1).5 The keywords used for the search string in the databases were these: (cybersecurity) AND (plastic surgery) AND (healthcare).
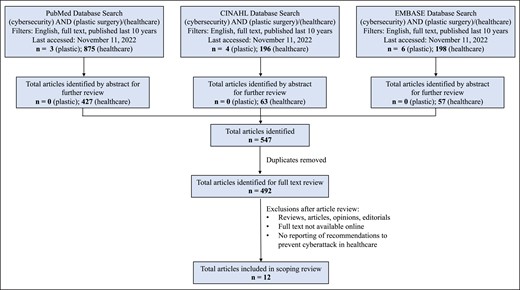
Flowchart of selection process for articles included in scoping review.
To be included in the review, manuscripts needed to discuss cybersecurity in plastic surgery or healthcare with a focus on preventive strategies for cyberattack. Peer-reviewed manuscripts were included if they were published between the period of 2012-2022, written in English, and available online. Articles were excluded if they were review articles, if they did not discuss cyberattack threat prevention in relation to plastic surgery or healthcare, and if the information was from magazines, newspapers, or editorials. The review was performed independently by 2 of the researchers. The results from each database search were exported in a document in which each reviewer separately listed eligible studies. In the case of disagreements, a third reviewer would review the paper independently. Extracted characteristics from eligible studies included findings and conclusions to optimize cybersecurity.
RESULTS
Survey
Of 89 individuals who began the survey, 69 completed it (77.5%). A total of 60 respondents either agreed or strongly agreed that cybersecurity is an important issue facing the plastic surgery community. The greatest perceived limitations for protecting against cyberattacks among plastic surgery practices were insufficient expertise (41.7%), followed by lack of funding and insufficient time to dedicate to this goal. Most respondents (78.7%) had cybersecurity policies incorporated into their practice, while 74.2% reported having dedicated technology to achieve said aims. Additional demographic data is summarized in Table 1.
| Author . | Synopsis . |
|---|---|
| Yeo LH, Banfield J6 | An exploratory analysis delving into the role of human security in healthcare breaches. Argues that human behavioral interventions such as staff education are a must in breach mitigation. |
| Priestman W, Anstis T, Sebire IG, Sridharan S, Sebire NJ7 | Conducted tests to assess the susceptibility of hospital staff to phishing emails. Shows high staff probability in interacting with phishing emails. |
| Martin G, Martin P, Hankin C, Darzi A, Kinross J8 | Discusses previous breaches in healthcare and current conditions that make healthcare so vulnerable. This source also proposes specific institutional change as a solution. |
| Bhuyan SS, Kabir UY, Escareno JM, et al9 | Explains the major types of cybersecurity threats as well as roles involved in mitigation and breaching processes. Authors also make recommendations for policy makers in aim of a healthcare security reform. |
| Pollini A, Callari TC, Tedeschi A, et al10 | Presents a human factors approach and how it affects cybersecurity risks in healthcare. Combines CIS computer technology and HF factors to make recommendations. |
| Niki O, Saira G, Arvind S, Mike D11 | Provides insight to the impact of cyber threats on staff well-being, arguing that cybersecurity education must be improved. The role of educators, policy makers, and organizations to employ this is outlined. |
| Perakslis E12 | Discusses data security objectives for medical practices with emphasis on importance of staff education and training in identifying and countering a cyberattack. |
| Blanke SJ, McGrady E13 | Proposed a checklist tool to monitor cybersecurity risks for health care facilities. The current information and sources of vulnerabilities were also noted. |
| Eichelberg M, Kleber K, Kämmerer M14 | Reviews prior PACS and medical imaging breaches with recommendations to mitigate cyber threats. The gaps in published literature are summarized. |
| Pope J15 | An overview describing the current questions clinicians and healthcare facilities have regarding breaches of privacy. Recommendations with legal perspectives are tabulated. |
| Lewis N, Connelly Y, Henkin G, Leibovich M, Akavia A16 | An assessment of attitudes, sentiment, and current norms are highlighted in aims to adopt new policy and healthcare professional education. |
| Ravi AR, Nair RR17 | A Lewin's field mapping approach is used to analyze current research and methods in mitigating strategies. Current defense mechanisms such as automatic robot procedures are also evaluated for their efficacy. |
| Author . | Synopsis . |
|---|---|
| Yeo LH, Banfield J6 | An exploratory analysis delving into the role of human security in healthcare breaches. Argues that human behavioral interventions such as staff education are a must in breach mitigation. |
| Priestman W, Anstis T, Sebire IG, Sridharan S, Sebire NJ7 | Conducted tests to assess the susceptibility of hospital staff to phishing emails. Shows high staff probability in interacting with phishing emails. |
| Martin G, Martin P, Hankin C, Darzi A, Kinross J8 | Discusses previous breaches in healthcare and current conditions that make healthcare so vulnerable. This source also proposes specific institutional change as a solution. |
| Bhuyan SS, Kabir UY, Escareno JM, et al9 | Explains the major types of cybersecurity threats as well as roles involved in mitigation and breaching processes. Authors also make recommendations for policy makers in aim of a healthcare security reform. |
| Pollini A, Callari TC, Tedeschi A, et al10 | Presents a human factors approach and how it affects cybersecurity risks in healthcare. Combines CIS computer technology and HF factors to make recommendations. |
| Niki O, Saira G, Arvind S, Mike D11 | Provides insight to the impact of cyber threats on staff well-being, arguing that cybersecurity education must be improved. The role of educators, policy makers, and organizations to employ this is outlined. |
| Perakslis E12 | Discusses data security objectives for medical practices with emphasis on importance of staff education and training in identifying and countering a cyberattack. |
| Blanke SJ, McGrady E13 | Proposed a checklist tool to monitor cybersecurity risks for health care facilities. The current information and sources of vulnerabilities were also noted. |
| Eichelberg M, Kleber K, Kämmerer M14 | Reviews prior PACS and medical imaging breaches with recommendations to mitigate cyber threats. The gaps in published literature are summarized. |
| Pope J15 | An overview describing the current questions clinicians and healthcare facilities have regarding breaches of privacy. Recommendations with legal perspectives are tabulated. |
| Lewis N, Connelly Y, Henkin G, Leibovich M, Akavia A16 | An assessment of attitudes, sentiment, and current norms are highlighted in aims to adopt new policy and healthcare professional education. |
| Ravi AR, Nair RR17 | A Lewin's field mapping approach is used to analyze current research and methods in mitigating strategies. Current defense mechanisms such as automatic robot procedures are also evaluated for their efficacy. |
Abbreviations: CSI, computer and information security; HF, holistic/human factors; PACS, picture archiving and communication systems.
| Author . | Synopsis . |
|---|---|
| Yeo LH, Banfield J6 | An exploratory analysis delving into the role of human security in healthcare breaches. Argues that human behavioral interventions such as staff education are a must in breach mitigation. |
| Priestman W, Anstis T, Sebire IG, Sridharan S, Sebire NJ7 | Conducted tests to assess the susceptibility of hospital staff to phishing emails. Shows high staff probability in interacting with phishing emails. |
| Martin G, Martin P, Hankin C, Darzi A, Kinross J8 | Discusses previous breaches in healthcare and current conditions that make healthcare so vulnerable. This source also proposes specific institutional change as a solution. |
| Bhuyan SS, Kabir UY, Escareno JM, et al9 | Explains the major types of cybersecurity threats as well as roles involved in mitigation and breaching processes. Authors also make recommendations for policy makers in aim of a healthcare security reform. |
| Pollini A, Callari TC, Tedeschi A, et al10 | Presents a human factors approach and how it affects cybersecurity risks in healthcare. Combines CIS computer technology and HF factors to make recommendations. |
| Niki O, Saira G, Arvind S, Mike D11 | Provides insight to the impact of cyber threats on staff well-being, arguing that cybersecurity education must be improved. The role of educators, policy makers, and organizations to employ this is outlined. |
| Perakslis E12 | Discusses data security objectives for medical practices with emphasis on importance of staff education and training in identifying and countering a cyberattack. |
| Blanke SJ, McGrady E13 | Proposed a checklist tool to monitor cybersecurity risks for health care facilities. The current information and sources of vulnerabilities were also noted. |
| Eichelberg M, Kleber K, Kämmerer M14 | Reviews prior PACS and medical imaging breaches with recommendations to mitigate cyber threats. The gaps in published literature are summarized. |
| Pope J15 | An overview describing the current questions clinicians and healthcare facilities have regarding breaches of privacy. Recommendations with legal perspectives are tabulated. |
| Lewis N, Connelly Y, Henkin G, Leibovich M, Akavia A16 | An assessment of attitudes, sentiment, and current norms are highlighted in aims to adopt new policy and healthcare professional education. |
| Ravi AR, Nair RR17 | A Lewin's field mapping approach is used to analyze current research and methods in mitigating strategies. Current defense mechanisms such as automatic robot procedures are also evaluated for their efficacy. |
| Author . | Synopsis . |
|---|---|
| Yeo LH, Banfield J6 | An exploratory analysis delving into the role of human security in healthcare breaches. Argues that human behavioral interventions such as staff education are a must in breach mitigation. |
| Priestman W, Anstis T, Sebire IG, Sridharan S, Sebire NJ7 | Conducted tests to assess the susceptibility of hospital staff to phishing emails. Shows high staff probability in interacting with phishing emails. |
| Martin G, Martin P, Hankin C, Darzi A, Kinross J8 | Discusses previous breaches in healthcare and current conditions that make healthcare so vulnerable. This source also proposes specific institutional change as a solution. |
| Bhuyan SS, Kabir UY, Escareno JM, et al9 | Explains the major types of cybersecurity threats as well as roles involved in mitigation and breaching processes. Authors also make recommendations for policy makers in aim of a healthcare security reform. |
| Pollini A, Callari TC, Tedeschi A, et al10 | Presents a human factors approach and how it affects cybersecurity risks in healthcare. Combines CIS computer technology and HF factors to make recommendations. |
| Niki O, Saira G, Arvind S, Mike D11 | Provides insight to the impact of cyber threats on staff well-being, arguing that cybersecurity education must be improved. The role of educators, policy makers, and organizations to employ this is outlined. |
| Perakslis E12 | Discusses data security objectives for medical practices with emphasis on importance of staff education and training in identifying and countering a cyberattack. |
| Blanke SJ, McGrady E13 | Proposed a checklist tool to monitor cybersecurity risks for health care facilities. The current information and sources of vulnerabilities were also noted. |
| Eichelberg M, Kleber K, Kämmerer M14 | Reviews prior PACS and medical imaging breaches with recommendations to mitigate cyber threats. The gaps in published literature are summarized. |
| Pope J15 | An overview describing the current questions clinicians and healthcare facilities have regarding breaches of privacy. Recommendations with legal perspectives are tabulated. |
| Lewis N, Connelly Y, Henkin G, Leibovich M, Akavia A16 | An assessment of attitudes, sentiment, and current norms are highlighted in aims to adopt new policy and healthcare professional education. |
| Ravi AR, Nair RR17 | A Lewin's field mapping approach is used to analyze current research and methods in mitigating strategies. Current defense mechanisms such as automatic robot procedures are also evaluated for their efficacy. |
Abbreviations: CSI, computer and information security; HF, holistic/human factors; PACS, picture archiving and communication systems.
Those who strongly agreed they had adequate technology to prevent data theft/breach were significantly more likely to be older than 55 years of age (P < .05), and surgeons in this age group were also significantly more likely to have formal policies in place to effectively prevent authorized patient data access, loss, and theft (P < .0001) as compared with respondents under the age of 55 (Figure 2 and Appendix). There were no differences in the likelihood of having a prevention policy or adequate protective technology against cyberattacks based on the practice's geographical region.
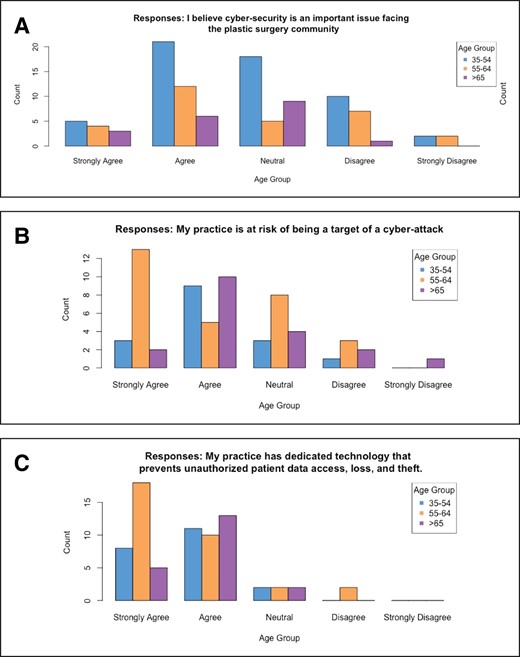
. Representative survey responses. (A) “I believe cyber-security is an important issue facing the plastic surgery community.” A total of 60 respondents agreed (n = 25) or strongly agreed (n = 35) with this statement. (B) “My practice is at risk of being a target of a cyber-attack.” Respondents older than 55 years of age (66 respondents total) were significantly more likely to “Strongly Agree” that their practice was at risk of cyberattack (P = .012), whereas younger age groups, under 55 years of age, were significantly more likely to “Strongly Disagree” and “Disagree” that their practice was at risk of a cyberattack (P < .0001 and < .0001). (C) “My practice has dedicated technology that prevents unauthorized patient data access, loss, and theft.” Respondents who strongly agreed with this statement were significantly more likely to be older than 55 years of age (P < .05) compared with younger age groups.
The perceived risk of a cyberattack was significantly lower among those respondents who “Strongly Disagreed” that they had a prominent social media presence (P < .05) and significantly higher among those who “Strongly Agreed” that they had a prominent social media presence (P < .01). Older physician respondents (age 55 and up) were significantly more likely to “Strongly Agree” that their practice was at risk of cyberattack (P < .05), whereas younger age groups, under 55 years of age, were significantly more likely to “Strongly Disagree” and “Disagree” that their practice was at risk of a cyberattack (P < .0001 and P < .0001).
Scoping Review
Database search and review of articles did not reveal eligible articles for inclusion pertaining to plastic surgery; however, 12 eligible articles regarding healthcare were identified and included in this review (Table 2) and incorporated into the following discussion.6-17 The articles identified acknowledge the growing threat of cyberattacks in healthcare and discuss actionable steps to mitigate an attack. Many articles described the human factor as being the essential deterrent for mitigating attacks. Legislation reform was also strongly advocated (Table 2).
| Variable . | N (%) . |
|---|---|
| Age group | |
| 35-54 | 23 (25.8%) |
| 55-64 | 32 (36.0%) |
| >65 | 21 (23.6%) |
| NA/declined to answer | 13 (14.6%) |
| Practice Region | |
| West | 24 (27.0%) |
| Midwest | 8 (9.0%) |
| South | 31 (34.8%) |
| Northeast | 13 (14.6%) |
| US Territories | 1 (1.1%) |
| NA/declined to answer | 12 (13.5%) |
| Practice Setting | |
| Solo private practice | 34 (38.2%) |
| Group private practice | 14 (15.7%) |
| Academic medical center | 2 (2.2%) |
| NA/declined to answer | 39 (43.8%) |
| Variable . | N (%) . |
|---|---|
| Age group | |
| 35-54 | 23 (25.8%) |
| 55-64 | 32 (36.0%) |
| >65 | 21 (23.6%) |
| NA/declined to answer | 13 (14.6%) |
| Practice Region | |
| West | 24 (27.0%) |
| Midwest | 8 (9.0%) |
| South | 31 (34.8%) |
| Northeast | 13 (14.6%) |
| US Territories | 1 (1.1%) |
| NA/declined to answer | 12 (13.5%) |
| Practice Setting | |
| Solo private practice | 34 (38.2%) |
| Group private practice | 14 (15.7%) |
| Academic medical center | 2 (2.2%) |
| NA/declined to answer | 39 (43.8%) |
Abbreviations: CSI, computer and information security; HF, holistic/human factors; PACS, picture archiving and communication systems.
| Variable . | N (%) . |
|---|---|
| Age group | |
| 35-54 | 23 (25.8%) |
| 55-64 | 32 (36.0%) |
| >65 | 21 (23.6%) |
| NA/declined to answer | 13 (14.6%) |
| Practice Region | |
| West | 24 (27.0%) |
| Midwest | 8 (9.0%) |
| South | 31 (34.8%) |
| Northeast | 13 (14.6%) |
| US Territories | 1 (1.1%) |
| NA/declined to answer | 12 (13.5%) |
| Practice Setting | |
| Solo private practice | 34 (38.2%) |
| Group private practice | 14 (15.7%) |
| Academic medical center | 2 (2.2%) |
| NA/declined to answer | 39 (43.8%) |
| Variable . | N (%) . |
|---|---|
| Age group | |
| 35-54 | 23 (25.8%) |
| 55-64 | 32 (36.0%) |
| >65 | 21 (23.6%) |
| NA/declined to answer | 13 (14.6%) |
| Practice Region | |
| West | 24 (27.0%) |
| Midwest | 8 (9.0%) |
| South | 31 (34.8%) |
| Northeast | 13 (14.6%) |
| US Territories | 1 (1.1%) |
| NA/declined to answer | 12 (13.5%) |
| Practice Setting | |
| Solo private practice | 34 (38.2%) |
| Group private practice | 14 (15.7%) |
| Academic medical center | 2 (2.2%) |
| NA/declined to answer | 39 (43.8%) |
Abbreviations: CSI, computer and information security; HF, holistic/human factors; PACS, picture archiving and communication systems.
DISCUSSION
Cyberattacks on healthcare entities are a growing security issue, having first been described in 1989 at a World Health Organization meeting in Sweden when a presiding speaker unwittingly distributed 20,000 ransomware-loaded floppy disks to attendees.4 More recently in 2014, Boston Children's Hospital suffered a week-long internet outage from a targeted denial-of-service attack.18 Since then, cyberattacks on healthcare institutions have grown in frequency, sophistication, and severity. Notably, the cost per data breach in healthcare has ranked highest among US infrastructure breaches over the past 12 years.1, 19 Aside from the severe economic costs of healthcare cyberattacks, the resulting violations of data and patient privacy threaten to erode patient trust in the healthcare system.20 The problem of cybersecurity is especially relevant in plastic surgery, a field dealing with highly personal reconstructive and cosmetic procedures for a wide array of patients. Our study is the first in the field of plastic and reconstructive surgery to investigate surgeons’ perceptions of cybersecurity threats, policies, and preventative strategies. This paper aims to deepen plastic surgeons’ understanding of cybersecurity threats and to equip them with knowledge and potential strategies to thwart attempted cyberattacks on their own practices.
Across the globe, efforts are underway to improve healthcare security infrastructure and to educate healthcare personnel to mitigate the harmful effects of cyber threats.7, 10–12 Unfortunately, there is no single strategy to completely protect against security threats. Our review identified several factors to mitigate risk. One basic, cost-effective technical safeguard that practices can implement is to ensure that devices are operating on regularly updated software, including anti-virus programs.15,16 Devices that rely on outdated software should be replaced,16 and secure data backups, whether manual or automatic, should be performed at least once a week (though preferably once every 24 hours).8 Encryption and de-identification of sensitive data should also be common practice when handling PHI, and protocols should be implemented to ensure that any data sharing is conducted through the safe and proper channels.13,15
In our review of the literature, many papers identified the human factor, rather than technology, as being the weak link in protection against cyberattacks. Yeo et al reported that proper healthcare cybersecurity contingency plans must go beyond technical controls to encompass human behavioral interventions. Through a review of breaches, it was found that a majority of human-factor–based breaches were due to carelessness, negligence, or apathy, often in response to cumbersome cyber policies or the perception that cybersecurity measures were too far removed from the practice's primary focus on patient outcomes.6 Furthermore, other research has revealed that a practice's managerial structure and culture, more so than a lack of cybersecurity knowledge, can predispose it to cyberattacks.10 Therefore, efforts have been implemented to establish cybersecurity-conscious practice environments where all employees feel a sense of duty to protect against breaches and where tools supporting employee work flow and cybersecurity policy compliance are optimized for excellent user experience. By creating a culture of accountability in which employees play an active role in improving security measures, where there is no risk of repercussion for reporting security-related incidents, and where critical information on cybersecurity efforts and preventative measures is regularly and widely circulated, organizations can marshal the collective efforts of their employees to better protect against devastating breaches and targeted cyberattacks.10,11
Though our study did not identify any significant differences among the various practice settings (group and solo private practice vs academic medical centers) in terms of surgeons’ perceived degree of risk and protection against cybersecurity breaches, it may be limited by the small sample size of academic and combined academic/private practice–based surgeons represented in our study. One study suggested there is no difference in cybersecurity awareness among healthcare professionals between the hospital and clinic setting.21 It has been suggested that US hospitals that are larger and classified as a teaching or pediatric hospital are more vulnerable to a data breach compared with other hospital settings.22 However, there are no specific reports of vulnerabilities in the outpatient setting specific to private practice. It can be inferred that private practices have less IT staff and a smaller budget compared with an academic institution, and therefore would be considered vulnerable to attacks. This is an area that needs further study as the literature is lacking in the private practice setting.
Our study noted surgeons older than 65 years of age were significantly more likely to report having adequate technology and policies in place to prevent a data breach compared with younger respondents. A study done by Seu et al found that older, more experienced plastic surgeons were less likely to use electronic health records (EHR).23 If the characteristics of this study are reflective to our study, this could explain older surgeons’ feeling more protected from cyberthreats. The literature has reported that younger adults (ages 18 to 30) are the most at risk regarding technology security awareness.24 This may be explained by a generation that is overfamiliar with tech and more likely to disregard basic cybersecurity practices. This is further supported by Alhuwail et al, who found that healthcare professionals with the greatest internet use were the least aware of cybersecurity policies and practices.21 This highlights the need for further education and resource availability for younger surgeons to optimize security in their practice.
Despite the clear and demonstrated risk of cyberattacks to plastic surgery practices, there is no resource to help practitioners quantify their cybersecurity risk exposure. This reality is especially concerning considering a recent report that 900,000 records from plastic surgery practices around the world were accessible simply by using a specific IP address owing to the data being saved on unsecured databases.25 As of January 3, 2023, a Google search of cybersecurity attacks in plastic surgery yields roughly four million results. According to Google Trends, search volume for cybersecurity has increased exponentially from January 1, 2004-2023.26 These results further illustrate the importance of strengthening current standards to protect PHI in healthcare. In 2018, the US federal government established The Cybersecurity and Infrastructure Security Agency27 to understand, manage, and reduce risks to cyber and physical infrastructure in the US. Specific to the medical field, the American Medical Association published an article outlining various cybersecurity threats and providing resources and recommendations to combat them.28 Cyber liability insurance has emerged as an increasingly necessary form of protection for physicians to employ in their practice. These insurance policies cover a wide array of security breaches, ranging from ransomware attacks to accidental loss of devices containing unencrypted patient information. Certain policies require payment of regulatory fines for penalties that may occur. The cost of cyber insurance has skyrocketed in recent years, with premiums rising yearly; however, policies are simultaneously scaling back many of their coverage limits.29
Social media is widely used by plastic surgeons to market their practice, educate patients, and network amongst colleagues.30 Social media profiles provide a wealth of information and data that is often open to the public, and users may be unaware of the associated security risks. The major risks are classified as social or technological. Social risks include inconsistent personal branding, reputational damage, and data breach. Technology risks include malicious software and unauthorized access to social media accounts.31
Major limitations to this study include a presumed poor response rate to the deployed survey (number of active email accounts and practicing surgeons is not known) and biases inherent to any survey-based study.32 In addition, further studies would investigate plastic surgeons’ cybersecurity practices according to specialties and according to those in academic and/or private practice settings. Further, no studies related specifically to plastic surgery were identified. Despite these drawbacks, knowledge gained from this study along with supporting review have led to the following recommendations to enhance cybersecurity practices.
Ensure Adequate Physical Mitigation Measures
Any server, computer, or portable storage device should be locked in a secure location, such as a dedicated room that is only accessible to employees with approved access. Further, these devices should be secured in a way to limit any movement (ie, enclosed server cabinet bolted to floor). Security cameras can further enhance security.14
Practice Good Cyber Hygiene
All devices in the practice should be password protected and require a new password every 6 months with 2-factor identification to access PHI. In addition, user access to files, folders, and networks that have PHI should be restricted to staff who require this information to perform their duties. All devices should automatically update to the latest version of firewall and anti-virus software. Data should be backed up to one’s server and/or cloud daily.13
Adopt an Acceptable Use Policy for Computer Use and Home Devices
All practices should adopt an acceptable use policy for use of computer equipment, software, email, and portable devices. Personal portable devices should be preapproved and comply with acceptable applications, including social media, that are allowed in the workplace. In addition, any device using PHI should be password protected with information encrypted. The use of any PHI being sent through personal devices or email should be prohibited.13 For additional information about personal use policies, SANS (SysAdmin, Audit, Network and Security) (North Bethesda, MD) has a template that can be modified for one's practice (https://www.sans.org/white-papers/369/).
Create a Security Awareness Culture
When defining cybersecurity policies and training among staff, it is important to promote an environment that encourages employees to report security-related incidents, without the risk of being blamed for violations that do not have malicious intent. It should be emphasized with staff that they are at the frontline of defense when it comes to protecting PHI. Increase staff's knowledge of how their actions impact security and seek feedback for how measures can be better implemented. Consider performing a yearly audit of your security measures and training to identify areas for improvement.10, 11
CONCLUSIONS
This study demonstrates the current policies for cybersecurity in healthcare are less than ideal. Despite increased federal oversight, healthcare and specifically small group or individual plastic surgery practices are vulnerable to cyberattack. Our survey reports the leading reasons for vulnerability being lack of funding, available resources, and knowledge to prevent a data breach. As technology advances, we must adapt to these evolving threats. The field of plastic surgery is known for finding solutions to address complex problems through innovation. It is imperative that we establish standards and protocols to help ensure we hold the highest level of protection for our patients.
Disclosures
The authors declared no potential conflicts of interest with respect to the research, authorship, and publication of this article.
Supplemental Material
This article contains supplemental material located online at www.aestheticsurgeryjournal.com.
Funding
The authors received no financial support for the research, authorship, and publication of this article.
REFERENCES
Cybersecurity & infrastructure security agency: about CISA. Accessed January 26, 2023. https://www.cisa.gov/about-cisa
Physician cybersecurity. Accessed January 26, 2023. https://www.ama-assn.org/practice-management/sustainability/physician-cybersecurity
Panaseer 2022 cyber insurance market trends report. July 2022. Accessed January 26, 2023. https://panaseer.com/wp-content/uploads/2022/07/2022-Cyber-Insurance-Market-Trends-Report.pdf
Author notes
Dr Hines is a plastic surgery resident, Department of Plastic Surgery, University of California, Irvine, CA, USA.
Dr Pfaff is a assistant professor of plastic surgery, Department of Plastic Surgery, University of California, Irvine, CA, USA.
Mr Trivedi is a undergraduate student, University of California, Berkeley, CA, USA.
Ms Hoang-Tran is a medical student, University of California Riverside School of Medicine, Riverside, CA, USA.
Mr Mocharnuk is a medical student, University of Pittsburgh School of Medicine, Pittsburgh, PA, USA.



